Understanding Phishing and Phishing Attacks

Introduction
Hello everyone, welcome to the “Phishing Diaries” series, which is a very detailed series about Phishing, Phishing attacks, sample attacks, methods, etc., which I have been planning for a long time but could not spare time but I am happy to finally bring you together with you. In this series, I aim to cover everything you need to know about Phishing attacks from a to z in detail and to have so much knowledge that you can be called an expert in Phishing. Welcome again, so let’s get started. Happy reading.
What is Phishing?
Phishing essentially means phishing, fishing. However, in the field of cyber security, this term is the name given to attacks against individuals, institutions and organizations for purposes such as fraud and information leakage. The correct usage is Phishing Attack.
If we elaborate a little more, it is a type of social engineering attack in which threat actors or malicious individuals or groups usually try to capture sensitive information of users through e-mails and fake websites and sms. Such attacks are usually based on gaining people’s trust and stealing their personal and sensitive information by making them click on fake but legitimate links. We will examine this topic in more detail in the future.
History of Phishing Attacks
To understand phishing attacks, we first need to understand their history. Phishing attacks date back to 1990, when the internet was just becoming widespread. In terms of word origin, phishing is a word derived from the word fishing. Because the attackers are trying to lure their victims to their own fishing line, just like fishing.
The first known phishing attacks targeted AOL in the United States. AOL targeted users of a service provider called America Online. This was the first phishing attack in history in which users’ information was stolen through a fake website.
Of course, these attacks have not diminished until today. Phishing attacks have become more sophisticated and evolved, especially as the internet has become more ubiquitous.
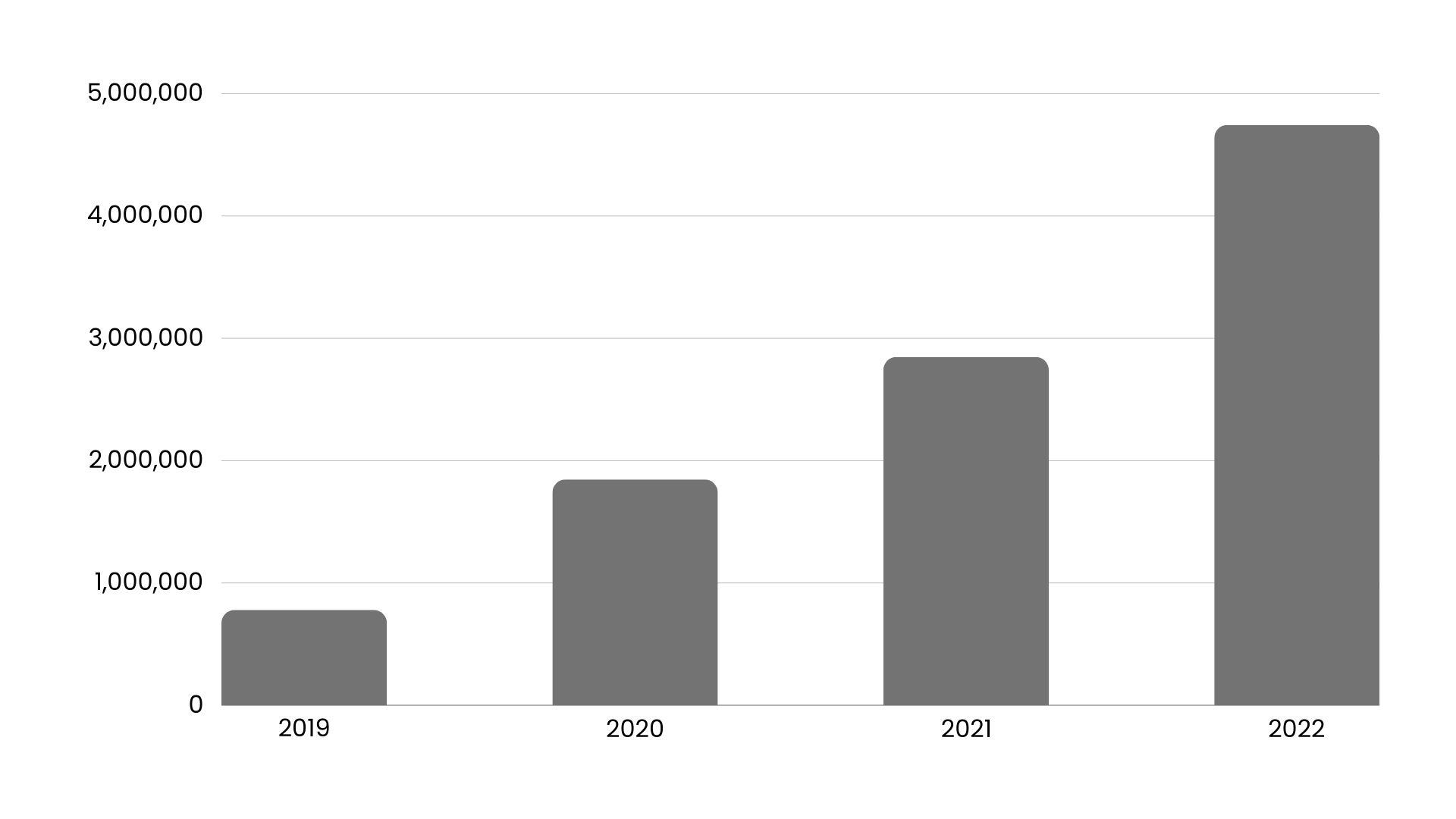
I wanted to show you the increase in phishing attacks over the years on a graph, especially because I thought it would be a good example. As you can see in this graph, the increase in attacks over the 4-year period from 2019 to 2022 is almost 400%! It’s a crazy number. But it’s real. (Source: XStation)
Today, phishing attacks especially target banks with the aim of stealing money. In addition to this, attacks continue to increase in various areas such as e-commerce sites, citizenship portals, etc. with various methods. In addition, while the target audience of the attackers has changed, the tools that play a role in phishing attacks such as e-mails, websites, and the design and content of the tools have become more convincing and difficult to distinguish. In fact, they are almost identical.
As an example, I am attaching two screenshots below, one of these login screens is the phishing website and the other is the real website.
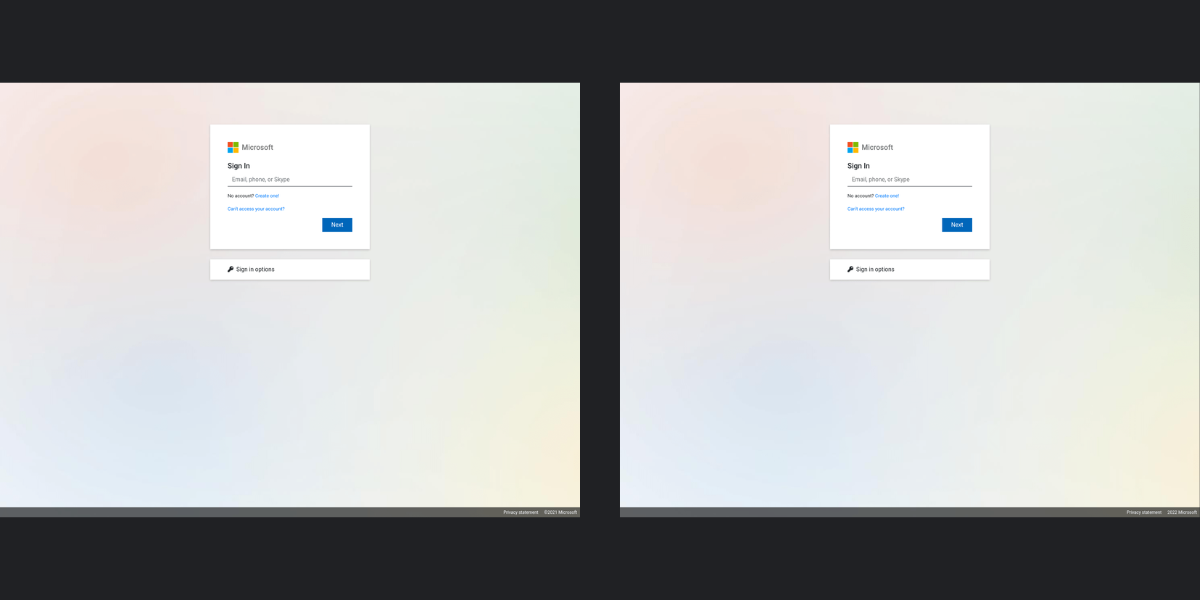
(Click!) Correct Answer
The site on the left is fake.The Evolution of Phishing Attacks from Past to Present
We’ve taken a brief look at the history of phishing, but the history of attacks is as old and sophisticated as its history.
To summarize briefly, when the internet was slowly becoming widespread, attackers were using fake websites and fake emails. Through emails, victims were directed to websites that looked legitimate. However, with the development of technology and the widespread use of social media, phishing attacks have started to be carried out through platforms. These have started to take on roles such as legitimate but fake accounts on the platform, fake advertisements that look legitimate.
With mobility and mobile devices becoming more widespread, attackers have developed mobile-based phishing techniques. QR Codes, mobile apps, fake links, sms and even voice messages! All of these are being carried out against victims by new attackers every day.
Since we are talking about QR Code based attacks, I would like to interrupt here and invite you to read the blog post “Unmasking QR Code Fraud Understanding the Threat” written by my dear teammate Alp Cihangir Aslan, which contains detailed information on QR code based phishing attacks.
You can click on the link below for the blog post:
Unmasking QR Code Fraud Understanding the Threat by Alp Cihangir Aslan
I take it you’re here? What a blog post… It was breathtaking. So let’s continue where we left off.
Today, all these attack methods, attack techniques and tools are developing day by day. In particular, we can say that artificial intelligence has a great contribution in this sense. Attackers using artificial intelligence and automation tools are conducting more sophisticated and targeted attacks day by day. Users are being deceived with tactics that seem more legitimate and more refined. Therefore, cybersecurity analysts and cyber threat researchers and hunters have much more work to do today.
Purpose of Phishing Attacks
From the past to the present, the internet and the ease with which it has made our lives easier has increased to an almost mesmerizing degree. With the rapid development of unconscious internet use and technology in the last 20 years, even though attacks have increased and methods have improved, the purpose of phishing attacks has remained the same as it was on the first day.
So what is this purpose? It is to lure you to websites and emails that look legitimate and get you hooked. In a nutshell, the purpose of phishing attacks is to capture your personal and sensitive information. Typically, the most common things attackers want to get from victims are;
- Usernames,
- Passwords
- Credit Card information,
- Bank account details,
- Nationality Numbers,
- etc.
And many more… And what can they do with this information? Attackers love money. Especially in phishing attacks carried out by individuals or groups motivated by money, the main target is the user’s credit card information. A screen and attack scenario in which you are asked to copy the interface of a bank, send an e-mail through an e-mail as if it were a bank, then click on it, redirect to a website that looks legitimate, and then request your information for bank login is often preferred. And as I said, there are hundreds of thousands, maybe millions of people who have fallen victim to financial fraud due to unconscious internet use or who have made purchases on their credit cards.
I hope that after completing this blog series, you will not be one of those who are exposed to those attacks; I believe that you will be an individual who detects attacks and takes the right actions, and I regret to say that we have come to the end of today’s blog post. Hope to see you in our next blog post, stay healthy.